Ultimate Security Guide
Comprehensive Security and Privacy Strategy for 2020
With the plight of the COVID-19 pandemic forcing people to digitize nearly all aspects of their lives, now is the perfect time for a general purpose guide to staying as safe as possible online. This guide has good pointers for just about anyone, but dissidents and journalists in particular should take particular note of this guide and fully implement the suggestions made below. I go highly in depth with application choice and best practices for privacy and security for desktop platforms as well as general services including those that bridge the online/offline divide. There will be two more parts that specifically address mobile phones and servers.
Web Browser
The web browser is likely the most heavily used software application for the vast majority of people and poses the greatest risk due to this fact and the rather large attack surface a browser engine has. There are really only several recommendations for web browsers that will preserve your privacy and security
- Mozilla Firefox (with some considerable user made edits)
- Ungoogled Chromium
- Brave
- Tor Browser Bundle (I’ll talk about it more in the Tor section)
Do not use Google Chrome, Safari, Opera, Vivaldi, Edge, or any other freemium browser. There are some more esoteric web browsers that are an apt choice for some edge cases like lynx; it
is a TUI browser that has support for the GOPHER protocol. For general web browsing, I recommend Firefox the most, but any one of the first 3 is ok. Regardless of browser choice,
DO NOT sign in with a google account. Firefox is a tried and true open source web browser that has the broadest feature set and the most granularity of control of any of the “normal”
browsers. Firefox can easily be hardened via a user.js file that specifies user preferences. While not a panacea, it can reduce the attack surface of the browser; I have my own user.js
linked here. To make it work, put it inside your browser profile (at $HOME/.mozilla/firefox/nameofprofile.something). As for extensions I recommend
for Firefox related to security:
- uBlock Origin or uMatrix (ad blocking/tracker protection; the latter can be overwhelming for power users, but I recommend it if you are capable)
- CanvasBlocker (prevents HTML5 canvas fingerprinting through spoofing)
- Cookie AutoDelete (automatically deletes cookies on pages that have been closed)
- Smart HTTPS (forces HTTPS on any site that might support it)
- CSS Exfil Protection (prevents CSS data leakage)
- Decentraleyes (prevents CDN tracking by locally emulating resources)
Ungoogled Chromium is a special build of the Chromium browser which Google Chrome is based on that strips all pre-compiled blobs, code from any google service, and features that restrict the user from having full transparency and control over the browser. It also adds some security and privacy related features. You can get it here. I highly recommend building it from source on a build server or on your own machine, but binaries are provided.
Brave is a Blink based browser (same engine as Chromium). It has several notable features, but the most salient is shields; it allows the user to customize the privacy controls applied to websites. These features are ad blocking, fingerprinting protection, cookie settings, connecting to HTTPS by default, and blocking javascript on a page. The user can configure both site specific shields and global defaults. There are a number of things I won’t go through in depth like Brave Rewards, which allow for users to earn money by watching private ads. That said, it’s feature set is pretty broad and even includes things like Tor mode, BitTorrent, and the ability to access IPFS natively.
Firefox has a great feature in the form of browser profiles. You can create separate profiles for various tasks to segregate the crossover sharing of data between different services. I recommend this approach if you’re not using Qubes (I talk about it in more detail below), in which case you can just make VMs for each task. I recommend having a general profile, a social media profile, a banking profile, and a shopping profile at least.
DNS
Unencrypted DNS traffic is analogous to a phone book filled with all the websites you’ve visited for your ISP or whoever runs your name servers. There are two protocols that have seen increased usage recently that encrypts DNS traffic: DNS over TLS (DoT) and DNS over HTTPS (DoH). Firefox has support for DoH, however, it is best to run a system daemon such as dnscrypt-proxy. You can get it in the package repositories of most Linux distributions as well as the FreeBSD and OpenBSD ports collection. If possible, it is best to run your own name server with dnscrypt-wrapper or unbound. Otherwise, there is a public list of servers you can use here.
Software as a Service Platforms (SaaS)
Search Engines
The choice of search engine is an important one as whoever the provider is can have a complete history of all of your search queries. Google is an obvious non-starter for their flagrant violations of privacy. Bing likewise is a poor choice for privacy, which should be no surprise as it’s in the Microsoft ecosystem. There are a myriad of search engines that are available that protect user privacy more than the likes of Google and Bing. The most popular of these is DuckDuckGo. It has all the bells and whistles you’d find in a modern search engine and it has improved considerably over time, especially with its image search. There are some caveats to its use; it isn’t entirely open source and it is under US jurisdiction. That said, it is available as a Tor hidden service, which is nothing to spit on. A non-US search engines with a good privacy policy is Qwant, which is based in France. They too suffer from the same folly of DuckDuckGo of not being open source. If you seek full autonomy over your search experience, Searx provides an extremely customizable experience. You can run your own instance or choose from a public list of instances. It is a meta search engine, meaning it aggregates queries from multiple search engines; which engines are used can be selected by the user in the preferences section of the site. If you want Google without any strings attached, use Whoogle. This yields vanilla Google results, but with no ads, user tracking, and some other features to increase privacy. You do have to host this yourself though, which out of the methods described in the readme, dockerizing it or deploying it normally to a VPS are probably the best options.
VPNs
A Virtual Private Network is a technology that allows a client to connect to a server’s private network via an encrypted channel in a way such that it’s as if the client was directly connected to the server’s network. Virtual Private Networks and Proxies are often heralded as magic security dust, when often they’re not. Many services that are free have significant strings attached in the form of limits on usage or data selling in the worst cases. Because customers can’t view the code running on servers, nor the network traffic, there is no guarantee of security and privacy being safeguarded. There was an incident with NordVPN last year that served as a sobering reminder that providers can do furtive things given the centralized nature of most VPNs. For these reasons, VPNs are often not a wise use of money for most people. There are some legitimate uses of VPNs, such as connecting to work intranets and for connecting over insecure public networks (i.e coffee shops). For those who want a VPN, it is best to run your own. One great solution is Algo, which is an automated set up for an IPSEC or WireGuard VPN. It requires your own VPS; you’ll want a privacy friendly provider like Njalla or PrivateAlps. Decentralized VPNs have become increasingly popular and mitigate some of the negative ramifications of traditional VPNs. Some examples of these are Mysterium and Lethean. There are some novel innovations that serve the same utility of a traditional VPN, but utilize different technology under the hood. One such project is Safing, which makes use of an onion-encrypted multi-hop mesh network that is dynamically generated.
Cloud Storage & File Sharing
Dropbox and Google Drive are the typical go to freemium services most people use for storing documents online. However, these services have some baggage for not having to pay. Namely the fact that they know exactly what you store and actively share it with third parties such as marketing firms and governments. There are better options for those who want more control, storage space, and privacy. The first option is that you can run your own cloud storage server with software such as Nextcloud. It provides a easy to use web client and isn’t too much of a hassle to set up. Another option that will satisfy most people’s need is Syncthing, which is a peer to peer file synchronization application which ensures that two or more configured devices have the same set of files in real time. This is arguably a better choice for those who don’t want to bother with managing a server and it even has support for NAT traversal, making it simple to quickly deploy to other devices on the same network.
Document collaboration
With Google Drive as everyone’s goto, this is a tougher one to replace. Cryptpad provides a highly robust, self-hostable, real-time document editor that is fully encrypted. It has a rich text editor, code editor, presentation creator, spreadsheet, poll creator, interactive whiteboard, encrypted cloud storage, and even a todo list. Another option for those who are running their own Nextcloud instance is to leverage the OnlyOffice integration. OnlyOffice is free and open source office productivity/collaboration software that can export to all Microsoft formats.
Email is of extremely high importance for a rock solid security and privacy strategy. Freemium web mail providers absolutely will not cut it; it is best to host your own (not recommended if you lack the technical aptitude) or to pay for an offshore mail provider such as Tutanota, Kolab, Riseup, and Posteo. The more you pay with these services, the more storage becomes available. Different services have varying features, so be sure to take an in depth look to figure out which provider best suits your needs. The free tier Tutanota account is my recommendation for those who can’t/don’t want to pay anything.
Choice of Client
Many email clients tend to be insecure by design, such as Mozilla Thunderbird. This is because they are nothing more than glorified web browsers that read email, leaving the attack surface of a browser engine in its wake. One of the most secure, lightweight mail clients is mutt. It is configured with plain text configuration files and is extremely customizable. My configuration with the personal information redacted looks like this:
## Mutt configuration -- ~/.muttrc
# General Settings
set header_cache = ~/.cache/mutt
unset imap_passive
set imap_keepalive = 300
set mail_check = 60
#set smtp_authenticators = 'gssapi:login'
set imap_check_subscribed
set mbox_type = Maildir
set editor = vim
set mailcap_path = ~/.mutt/mailcap
#auto_view text/html # view html automatically
## Work
source "~/.mutt/work"
folder-hook $folder 'source ~/.mutt/work'
## Personal
source "~/.mutt/personal"
folder-hook $folder 'source ~/.mutt/personal'
## Aliases
set alias_file = "~/.mutt/aliases"
set sort_alias = alias
set reverse_alias = yes
source $alias_file
## Encryption
source ~/.mutt/gpg.rc
## Shortcuts
macro index,pager <f7> '<sync-mailbox><enter-command>source ~/.mutt/personal<enter><change-folder>!<enter>'
macro index,pager <f8> '<sync-mailbox><enter-command>source ~/.mutt/work<enter><change-folder>!<enter>'
## Personal Profile
## Receive options.
set imap_user = jdoe@sample.com
set folder = imaps://sample.com
set spoolfile = +INBOX
set postponed = +Drafts
set record = +Sent
## Send options.
set smtp_url = smtps://$imap_user:$imap_pass@sample.com
set realname = 'John Doe'
set from = jdoe@sample.com
set hostname = "sample.com"
set signature = "John"
## Hook -- IMPORTANT!
account-hook $folder "set imap_user = jdoe@sample.com"
For aliases in mutt, you can set a file in the general configuration file and the syntax is
alias nick bob.johnson@example.net
Mutt doesn’t natively support viewing html emails and I recommend against viewing html emails as they’re a security risk.
If you must absolutely view it, then uncomment the auto_view text/html line in my general configuration. Then, install the lynx browser via your package manager and add a file called
mailcap in ~/.mutt:
# Mailcap
text/html; lynx -assume_charset=%{charset} -display_charset=utf-8 -dump %s; nametemplate=%s.html; copiousoutput
Now mutt will dump raw html into the client when a received message is formatted in html.
Email Encryption
Email encryption is best done with GNU Privacy Guard. Just grab it from your package repository and run gpg --full-key-gen which will run you through a text based key generation wizard
that lets you set the parameters you want. Make sure to choose a key length of 4096 bits. After you’ve done that, you can view your key pair (and any others you add to your keyring) with
the command gpg --list-keys. To import someone’s public key, run gpg --import their-public.key. Make sure to back up your own public key by running gpg --output your-public.key --armor --export userid. It is trivial to configure gpg email encryption in mutt; make a gpg.rc file and source in the main configuration. The file should look something like
# gpg.rc
# Use GPGME
set crypt_use_gpgme=yes
set crypt_autosign = yes
set pgp_sign_as = thestringofnumbersthatisyourpublickey
set pgp_timeout = 3600
set pgp_good_sign="^gpgv?: Good signature from "
# Sign replies to signed email
set crypt_replysign = yes
# Encrypt replies to encrypted email
set crypt_replyencrypt = yes
# Encrypt and sign replies to encrypted and signed email
set crypt_replysignencrypted = yes
# Attempt to verify email signatures automatically
set crypt_verify_sig = yes
# Autosign all email
set pgp_autosign=yes
Disposable addresses
It is frequently the case that our email is demanded whilst creating an account for online services. It’s not always wise to give your real email to these services; instead, one can use a throwaway email account. This is best done with an online service like Mailinator or Nada. With both of these sites, you can instantly spin up a temporary inbox and use it to sign up and once you’re done, closing out of the service will destroy the inbox. Make sure to save the email name somewhere so you remember it for login purposes!
Communications
Most messaging and Voice Over IP (VOIP) protocols, clients, and services are extremely invasive and have both terrible privacy and security. If you use a common platform, chances are it sucks and you need to replace it. Discord is an absolute no go as they refuse to provide end-to-end encryption and inspects transient VOIP data and other user data. Furthermore, it is a fully centralized service, taking away any ability for true user discretion. It is best to outright avoid this platform or at the very least not say or send any sensitive information over it. Likewise with Zoom, which has a myriad of problems.
For VOIP, Mumble is a lightweight and versatile application that has outstanding voice quality and low latency (highly optimal for gaming). It is self-hostable and very easy to set up as well and I may create a guide for how to set up a mumble server of your own. For administrators of the server, mumble has an elegant permission scheme via ACLs (Access Control Lists). All communications to and from the server are encrypted; chat messages are encrypted with 256 bit AES in Galois Counter Mode (GCM) with a SHA-384 hash over TLS. Voice data is encrypted with 128 bit AES in Offset Codebook Mode (OCB). Mumble uses public/private key user certificates for authentication between client and server.
For messaging clients, there are a couple of salient options. The first is using XMPP with the OMEMO encryption extension. This borrows the Double Ratchet Algorithm from Open Whisper Systems (developers of Signal, which we’ll talk about). A couple of clients that support OMEMO are Gajim and Profanity. Gajim is highly feature rich and supports among many other plugins, OMEMO. It is best to either run your own XMPP server like ejabberd or prosody to use; if you can’t, choose from servers from this list, though it’s best to vet them thoroughly. If you are to choose any service on there, creep.im is what I’d vouch for. Signal Desktop from Open Whisper Systems is also a venerable choice, however, it does have the drawback of being a centralized service and the desktop verson lacks the more expansive feature set of the mobile version (which we’ll discuss more in part 2). I build and maintain my own AppImage builds for Signal Desktop, which I may make publicly available if there is enough support, but I’ll show how to build it from source here (you need nvm for this to work):
git clone https://github.com/signalapp/Signal-Desktop && cd Signal-Desktop
git checkout tags/v1.34.3 # Or whatever the latest release is when reading
nvm use
nvm install version # Only if you don't yet have that version installed
npm install --global yarn
yarn install --frozen-lockfile
yarn grunt
yarn generate
yarn build-release
cd release
UPDATE: In 2021, you need to install git-lfs and run git-lfs install to build Signal desktop.
If you want to build the AppImage, you must choose AppImage as a target in the package.json file like this:

For a solid replacement for Zoom, Jitsi is leagues ahead of the competition. It runs in a web browser and has support for voice, video, screensharing, collaborative document editing via EtherPad, SIP support so that you can call in by phone, and is accountless by design. It is self hostable so that administrators have maximum control over their rooms. They’re even working to implement end to end encryption on top of the encrypted connection to the instance and back using a new feature in WebRTC called insertable streams.
Operating System
The choice of operating system is extremely important and often dismissed by the average user. Any version of Windows is an inappropriate choice for privacy and security for many reasons. MacOS is also not much better for security. Beyond the linked resources, neither OS is secure by design. The best choice for an OS is a reasonably secure by default UNIX-like OS. This includes most (but not all) Linux distributions as well as the BSDs and some other ones most people probably haven’t heard of. There are too many Linux distributions to count, but some that I’d recommend are
- Debian/Devuan
- Fedora
- OpenSUSE
- Qubes
- Arch Linux
- Void Linux
- Alpine Linux
- Gentoo
- Slackware
Some non-Linux OSs can be a great option depending on use case and expertise too. Some of these are
- FreeBSD
- OpenBSD
- NetBSD
- DragonFly BSD
- A lot of the Illumos based stuff like OpenIndiana, SmartOS, OmniOS, and Tribblix
For the typical power user, Debian is what I’d try first. It’s highly reliable and rich with software in its software repositories. They also have their own self-hosted Tor mirrors too for those interested. OpenSUSE and Fedora are great choices too and both are highly innovative in the open source space; the tumbleweed variant of OpenSUSE and Fedora are decent choices for software developers who want the latest and greatest on systems that are still fairly reliable. Qubes is a specialized operating system that is focused on security through the principle of security by compartmentalization. It makes use of the Xen hypervisor to create isolated virtual machines for the purposes of isolating different groups of tasks; it has by default a work VM, a personal VM, and an untrusted VM. Users can create as many VMs as they want and they can even be disposable; this is an especially good option to use in conjunction with the Tor Browser Bundle. The amount of options in Qubes will quickly overwhelm most users, who will want to read the documentation to learn more. The remaining five options I listed for Linux are for adept Linux users who want high granularity of control over their operating system and want something that is light weight relative to other Linux distros (which are light to begin with!).
The BSDs can be a good choice for some users. FreeBSD is a general purpose operating system that is highly performant (comparable to Linux) and is particularly good in the networking department. It is a good choice for desktop and server alike, and while it has generally good security, it has only recently merged ASLR support into FreeBSD 13-CURRENT. OpenBSD is arguably the most secure by default of any of the OSs I listed. They have an emphasis on portability, code correctness, and rock solid security. They have been pioneers of many security innovations, including OpenSSH, write xor execute, pledge, position-independent-executables, and many more.
Disk Encryption
Being bereft of disk encryption is like leaving all the windows and doors to your house wide open; a strong user/sudo/doas password is insufficient to keep your data safe. Luckily, it’s
trivial to set up full disk encryption in UNIX-like operating systems. On Linux, the best option is Linux Unified Key Setup with dm-crypt via the cryptsetup tool. For newbie users,
there is no need to worry with making use of it directly as Debian, Fedora, OpenSUSE have graphical installers which greatly aid in setting it up. For manual setup as required in Arch
Linux, Void Linux, Gentoo, Slackware, and most other more advanced distribution of Linux, I will walk through an example below. I assume all commands are ran as root on a UEFI system
and that we make use of Logical Volume Management (LVM):
gdisk /dev/sdX # X is whatever the device name is and gdisk helps us partition. We're going to make a 200MB ESP partition mounted at /boot and another one that uses the rest of the space
cryptsetup luksFormat /dev/sdX2 # Initializes the partition for LUKS where we set up a password among other things
cryptsetup luksOpen /dev/sdX enc # Makes the LUKS container decrypted and available for use at /dev/mapper/enc
pvcreate /dev/mapper/enc # Initializes a physical volume on the system partition
vgcreate Linux /dev/mapper/enc # Creates a volume group called Linux on the newly created physical volume
lvcreate -L 10G -n root Linux # Creates a logical volume of size 20GB called root within the Linux volume group
lvcreate -l 100%FREE -n home Linux # Creates a logical volume that uses the rest of the space on the physical volume called root within the Linux volume group
mkfs.vfat -F32 /dev/sdX1 # Formats the ESP partition to FAT32
mkfs.ext4 /dev/mapper/Linux-root # Formats the root logical volume to the EXT4 filesystem
mkfs.ext4 /dev/mapper/Linux-home # Formats the home logical volume to the EXT4 filesystem
I purposefully left the creation of a swap partition as modern systems with SSDs and ample RAM don’t need one. Regarding the boot partition, users are prone to evil maid attacks if there are adept adversaries that could have physical access to the device readily. This is where an attacker alters the user’s computer in a subtle way to later gain access to it. In the case of an unencrypted boot partition, an assailant could install malware or tamper with it in some other way There are two ways to mitigate this attack vector: install the boot partition on a removable drive like a usb stick, encrypt it, or securely store the device in a safe when unattended (especially in the case of a laptop). When using LUKS, keep in mind that the GRUB bootloader doesn’t support LUKS2, so to setup an encrypted boot, we’d run
cryptsetup luksFormat --type luks1 /dev/sdX1
cryptsetup luksOpen /dev/sdX1
With FreeBSD, GELI is the best bet and the FreeBSD handbook does a great walkthrough for it. OpenBSD makes use of softraid and bioctl for full disk encryption which the official FAQ describes.
File Encryption
File encryption is straight forward on UNIX likes too. There are a few tools handy for the job. GNU Privacy Guard (gpg) has the option to symmetrically encrypt files:
gpg -c --s2k-cipher-algo AES256 --s2k-digest-algo SHA512 --s2k-count 65536 myfile # Encrypts
gpg --output myfile --decrypt myfile.gpg
7zip can encrypt archives as well. This is highly useful if you’re using a freemium cloud storage service, but want to keep your files secure and away from prying eyes. Using the cli client for 7zip (p7zip), we can create an encrypted archive with AES-256 encryption with the command
7z a -t7z -m0=lzma2 -mx=9 -mfb=64 -md=32m -ms=on -mhe=on -p'mystrongpassword' my-archive.7z dir
Last, there is tomb, which is a utility that can create encrypted directories that are opened and closed with key files associated with them along with a passphrase. The official website has more information on usage.
Sandboxing
Isolating applications from accessing kernel resources is very important to stopping downloaded malware. If nothing else, sandboxing any application you don’t need internet access for
as well as your image viewer and pdf viewer should be a minimum. If you’re using Qubes OS, skip this section. For Linux, I recommend using Firejail,
which is a lightweight SUID sandbox that uses seccomp and Linux namespaces. There are built in profiles for most major applications and to run an application with firejail by default,
run ln -s /usr/bin/firejail /usr/local/bin/app as root. To have all available applications with profiles run with firejail by default, run firecfg. In FreeBSD, there are jails.
These are chroots on steroids. They can be used to run isolated services or emulate a full FreeBSD system. With the ZFS file system, we can make a dataset for the jails to reside in:
zfs create -o mountpoint=/usr/local/jails zroot/jails
zfs create zroot/jails/complete-jail
Then, choose one of the methods elucidated in the handbook for installing a jail. You can then start the jail by running jail -c nameofjail. All jails can be configured at
/etc/jails.conf and they will all start at boot if the option jail_enable="YES" is added to /etc/rc.conf. The man page for jail.conf can be read here.
There is jexec for running commands in a jail and jls for listing all active jails. FreeBSD also boasts a technology called Capsicum, which is a process sandboxing framework. Its
core feature set is centered around capabilities and capability mode; they are refined file descriptors whose permissions can be finely tuned and a sandbox that blocks access to global
namespaces respectively.
General Hardening
There are steps that all users should take to make their Operating System more resilient. If you’re on Windows, it’s probably best just to use something else. For Linux users, significant steps can be taken to improve the security of your installation by modifying sysctl flags. These tighten down what the kernel can do. They are modified by specifying them at /etc/sysctl.conf. My configuration looks like this:
### /etc/sysctl.conf ###
## Kernel
# Controls the System Request debugging functionality
kernel.sysrq = 0
# Restrictions on the viewability of kernel addresses
kernel.kptr_restrict = 2
# Enlarge the PID space
kernel.pid_max = 65536
## Network
# Log packets with impossible addresses
net.ipv4.conf.all.log_martians = 1
net.ipv4.conf.default.log_martians = 1
# Enable strict mode for reverse path filtering
net.ipv4.conf.all.rp_filter = 1
# This isn't a router!
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv6.conf.default.accept_redirects = 0
net.ipv6.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_source_route = 0
net.ipv6.conf.all.accept_source_route = 0
# Ignore all ICMP ECHO and TIMESTAMP requests sent to it via broadcast/multicast
net.ipv4.icmp_echo_ignore_broadcasts = 1
# Prevent against syn flood attacks
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_synack_retries = 5
# RFC 1337 fix
net.ipv4.tcp_rfc1337=1
## Filesystem
# Increase file descriptor limit
fs.file-max = 65535
FreeBSD has a number of hardening options that can be set during installation at the system hardening dialog box.

FreeBSD also has the ability to tune sysctl flags as well. Some of these are automatically set when selecting some of the options in the installation menu. In /etc/rc.conf, add the lines
## /etc/rc.conf
kern_securelevel_enable="YES"
kern_securelevel="2"
You can read more about what the levels mean here. Available to all UNIX-like operating systems is an auditing tool called Lynis. It is a shell script that runs through various checks related to having a secure system. It generates a score and shows the result of each scan as well as a list of suggestions. Some of these are not pertinent to desktop usage, so they can be safely ignored.
MAT2 is a tool that strips the metadata from files, which can be used to identify the “who, what, when, where, and why” of the documented data. It can be used in its cli form or as an extension for the Nautilus file manager.
Firewall
Part of any reasonable security setup include a well written firewall. On Linux, nftables has been perfectly stable at least since kernel 4.9 if not earlier; time to ditch iptables if you’re still using that. For a standard desktop, the following nftables configuration is adequate:
#!/usr/bin/nft -f
flush ruleset
table inet filter {
chain input {
type filter hook input priority 0;
# accept any localhost traffic
iif lo accept
# accept traffic originated from us
ct state established,related accept
# drop invalid connections
ct state invalid drop
# services
#tcp dport { 22, 53 } ct state new accept
#udp dport { 53 } ct state new accept
# accept neighborhood discovery
ip6 nexthdr icmpv6 icmpv6 type { nd-neighbor-solicit, nd-router-advert, nd-neighbor-advert } accept
# count and drop all other traffic
counter drop
}
chain forward {
# Drop anything forwarded to the box
type filter hook forward priority 0; policy drop;
}
chain output {
# Accept outbound connections
type filter hook output priority 0; policy accept;
}
}
There are far more options here than I will go through in this guide. Read the wiki to learn more. For FreeBSD and OpenBSD, I wholeheartedly recommend packet filter (pf). It is one of the best firewall frameworks I’ve used and it’s one of the crowning jewels of the OpenBSD project. Note that FreeBSD’s version is not the same as the vanilla one on OpenBSD and lags behind it. For FreeBSD, a basic workstation configuration might look like this:
# /etc/pf.conf
# The primary network interface being used
ext_if="re0"
# Services
#tcp_services = "{ssh, http}"
#udp_services = "{8000:8005}"
# We allow some ICMP traffic for things like neighborhood discovery
icmp_types="{echoreq, unreach}"
icmp6_types="{echoreq, unreach, 133, 134, 135, 136, 137}"
# Randomize sequence numbers
tcp_state="flags S/SA keep state"
udp_state="keep state"
# Drop rejections
set block-policy drop
# Allow loopback
set skip on lo0
# Incoming traffic on the primary interface is normalized and fragmented
scrub in on $ext_if if all fragment reassemble
# Default deny
block in log all
# Allow outbound
pass out quick modulate state
# Enable antispoofing for the primary interface
antispoof for $ext_if inet
antispoof for $ext_if inet6
# Block packets failing reverse path check
block in from urpf-failed to any
# Drop broadcast requests
block in quick on $ext_if from any to 255.255.255.255
# Allow services specified above
pass in on $ext_if inet proto tcp from any to any port $tcp_services $tcp_state
pass in on $ext_if inet6 proto tcp from any to any port $tcp_services $tcp_state
pass in on $ext_if inet proto udp from any to any port $udp_services $udp_state
pass in on $ext_if inet6 proto udp from any to any port $udp_services $udp_state
# Allow ICMP
pass inet proto icmp all icmp-type $icmp_types keep state
pass inet6 proto icmp all icmp-type $icmp6_types keep state
A similar set up could be used for OpenBSD.
Secure deletion
For this task, there is no better tool than Bleachbit. It deletes unnecessary files automatically and can overwrite the contents of files. It can also be used to permanently remove files and directories.
Password Management
One of the most profound risks to your security and having your identity stolen are shoddy, weak passwords for accounts. Most people have appallingly short passwords that don’t make use of a broad variety of character types. Moreover, many people recycle the same weak password for all or most of their accounts. If one hackers breaches a compromised website (happens often on sites where they don’t hash and salt their stored passwords), all of your accounts could be accessed, especially if you use the same email for other accounts. The best way to safeguard yourself against such risks is to use a high quality password manager that can make strong, unique passwords for most of your accounts. Rather than having to remember 50 passwords, you only need to remember the master password to the database and your user and disk encryption passwords. Browser based options like LastPass are problematic as they are far more susceptible to malware and network attacks. It’s better to use a local, offline password manager. My recommendation is KeePassXC. It is open source and can always be used fully offline and stores passwords in an encrypted database that you can backup. It also allows for the creation of a key file, without which the database will not open. This allows for a setup where the user has the key file on a mounted USB stick and the database is on the computer. If one is truly paranoid and has concerns about the quality of code in KeePassXC and wants fully transparency in their password management, a spartan solution is to draft a text document with all of your accounts and corresponding usernames and passwords, then encrypting with gpg. As mentioned earlier, it is best to use disposable emails whenever possible when making accounts. Last point of note is to always choose long passphrases with all character sets. You should choose a minimum of 20 characters, but can and should choose much higher.
Credit Cards
Credit cards are the world’s ubiquitous surveillance devices. Credit card companies have plenary knowledge on information pertinent to any purchase made with the card; this can be used to construct a robust profile of the person in question with the creditor knowing what was bought and where. Most of the same concerns exist with debit cards as well. We can reap the benefits of a cashless society without sacrificing privacy. Cryptocurrencies have a reputation of being highly volatile, speculative assets. That said, there is a kind of currency called a stable coin, which is a cryptocurrency designed to have a 1:1 conversion ratio with the US Dollar. The most popular of these is called tether, though it’s been marred with scandal
Two better options in my opinion are USD Coin and Dai. Both are open source and the latter is decentralized. These are both ERC20 tokens, so they’re compatible with any wallet that has support for Etherium in theory. Some examples of these are Coinomi and Guarda. These are both open source and available on mobile platforms as well as Windows, Mac, and Linux. There are also hardware wallets like Ledger that add an extra security layer by having the private keys of the user stored on an external device to prevent them from being compromised on a far less secure smartphone or possibly desktop computer.
Tor
Tor is an anonymous network that is designed to protect anonymity with respect to the user’s location and activities through being highly resistant to network traffic analysis or surveillance. The Tor Browser Bundle is the centerpiece of the ecosystem and can be downloaded here. There are a few things to keep in mind while using Tor in general
- Don’t ever use your real name or any information that could identify you. This includes usernames that are used on the clearnet
- If possible, consider using Tor in Qubes, TAILS, and Whonix
- Don’t bother using it on Windows or your phone; if you must use Windows as a host, run Tor in Whonix
- Never add any additional extensions to TBB or change any setting unless you know exactly what you’re doing
- It is best to move the security slider to safest
- If you wish to buy goods or services, use Monero
- Use a Tor hidden service email account if you feel the need to use an email for forums or other purposes (it’s almost never required to begin with!)
- Use gpg or pgp encryption and verify signatures
- If you need to message a buyer and they don’t communicate over email, use XMPP w/OMEMO over Tor with a solid client like Gajim
- Don’t maximize the browser window
- Don’t access clearnet accounts such as ones for social media over Tor
- Always make sure you’re using the latest version of the browser
- Vary your writing style on forums and elsewhere to avoid being detected through stylometry (i.e vary your vocabulary and alter sentence structure)
Regarding point 2, TAILS and Whonix are two operating systems specialized to securely run Tor through. While both similar in purpose, they work very differently; TAILS is a live system that is booted into that wipes all data on shutdown and reboot and Whonix is a pair of virtual machines that are designed to make sure that critical user information is never leaked to an attacker. The most prudent choice boils down to what your greatest threat is. Whonix is a superb choice for those who worry most about their ISP and/or remote attacker. TAILS is best suited for those who want to use Tor without any physical trace and/or may need to use another person’s computer on occasion. If you make use of Whonix or TAILS, all installed applications are already designed to run over Tor.
To illustrate how Tor works, below is a simple diagram that showcases how traffic moves through Tor. Connections within the network are fully encrypted, however, any traffic exiting the network to the clearnet via an exit node is not encrypted and is subject to network traffic analysis:
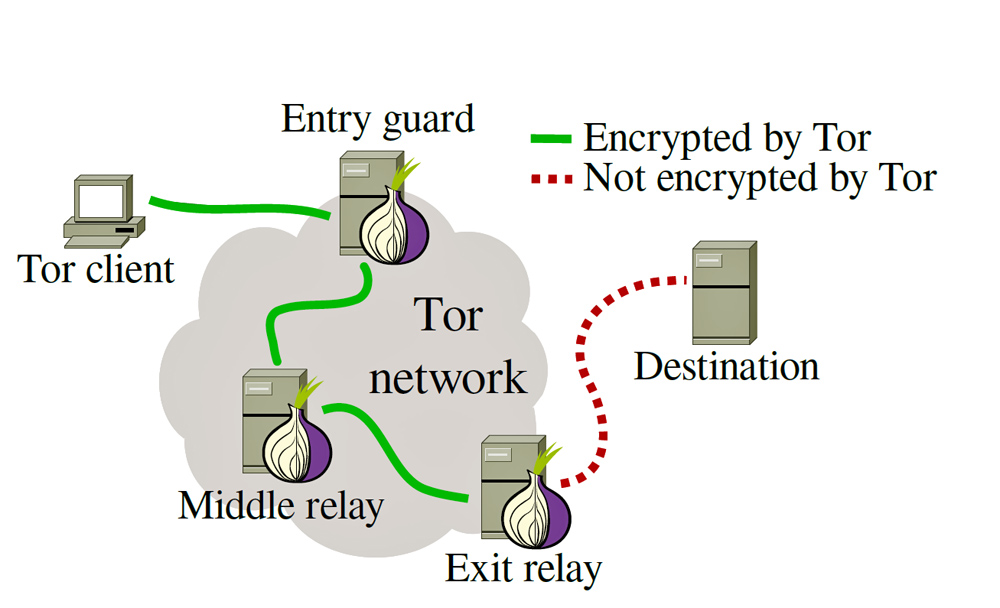
Intranetwork connections enjoy more hops whereas connections to the clearnet move through 3 relays before exiting. If you live under the regime of a hostile government, it is wise to use Tor over a bridge, which is an unlisted Tor relay. In the setup wizard for TBB, you select the option that says “My ISP blocks Tor”. Then, choose the obfs4 pluggable transport and pick the provided bridges unless you’re running your own bridge(s) for yourself.
For journalists and political dissidents, Onion Share is a great tool for anonymously sharing information with media organizations and others securely.
Torify Those Things!
If you want to “Torify” network services outside of the TBB and you’re not using TAILS, Whonix, or Qubes, run the tor daemon locally on your system. You can then go into your network
facing applications like Gajim and go to the proxy settings. Select SOCKS5 proxy and choose the address to be 127.0.0.1 and the port to be 9050. Commandline applications can also be
easily torified through the use of the torsocks command. For example, if I wanted to use curl to download something over Tor, I would run torsocks curl -O somelink.onion .
More to come
I will have a second part that covers offline OPSEC and the use of social media and mobile phones and a third part about securing servers as well as your own home network.